How to Block Personal OneDrive

Problem
I wanted to block access to personal OneDrive or any other personal Microsoft365 portals without disrupting any access to legit company resources. i.e. only allow access to your corporate OneDrive.
Why?
To mitigate the risk of data exfiltration by users or attackers who have compromised a user account.
Options
- Block access to Microsoft domains. e.g. onedrive.live.com
BUT this will block access to OneDrive completely for everyone. Crazy business disruption.
- Block Access to OneDrive for everyone except specific user groups
BUT this will still give access to personal OneDrive and the like for the users that have exceptions. Risk of Data Exfil is still significant. Also, it’s just messy and hard to manage and scale.
Need something more elegant.
Need to somehow tag all legitimate business traffic to the Company 365 portals and block everything that isn’t.
Turns out there is a way, Tenant Restrictions for SaaS apps.
How does it work?
All the traffic destined for Microsoft 365/Entra will have some specific HTTP headers injected into the requests, effectively tagging the requests.
In our proxy infrastructure, I set up rules to inject the following headers to traffic going to Microsoft Apps.
If you are using V1 (enforcement is at the proxy), use these headers:
Restrict-Access-To-Tenants: <domain name>
Restrict-Access-Context: <Entra Tenant ID>
sec-Restrict-Tenant-Access-Policy: restrict-msa
The last one is important to block consumer apps like OneDrive which is what I am after.
If you are using V2 (there are cross tenant policies in Entra already), use this header:
sec-Restrict-Tenant-Access-Policy:<tenant ID>:<policy ID>
So all M365 traffic is now tagged with unique tenant specific identifiers.
After some trial and error, ( a few days with lots of testing and head scratching) I got this working nicely. Here is what the user sees when they try to access a non-work OneDrive.

This solution is neat, elegant and causes minimal business disruption.
The good thing about Tenant Restrictions is that it doesn’t just apply to M365. I can block access to other personal SaaS apps like Google Suite, Slack, Dropbox etc using their own specific headers. These are all legit business apps but ones you may want to restrict access to neatly.
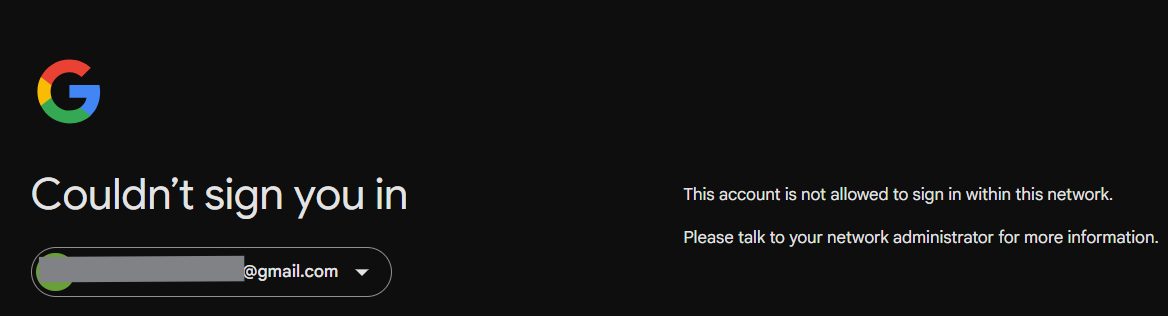
For example, used this header to block non-work Google Apps access:
X-GooGApps-Allowed-Domains:<approved domain name>
Users accessing personal Gmail now see this:
TIPS
- To make this work, TLS Inspection needs to be enabled so that the headers can be inspected.
- Even if TLS Inspection is enabled, beware of bypass rules causing some traffic to bypass inspection. Ensure your intended traffic is actually being inspected.
- Make sure you are using the correct header formats according to whether you should be using V1 or V2.
- Test different scenarios. Fresh sign ins, re sign ins, page refresh, close browsers , incognito.
Next: How can we stop the headers being spoofed?



