ETags

We got a Critical alert that a certain port is exposed on an IP address apparently linked to our organisation.
The alert reported that the service is vulnerable to high severity vulnerabilities and listed all the CVEs and techniques associated to them.
My initial thought was this doesn’t look like one of our IPs.
The details of the alert come from Shodan. I searched the IP address on Shodan and all the general information returned was not related to us.
I narrowed the search by port and found something called ETag in the HTTP response header.
The ETag listed what looked like a hash. What’s an ETag? Here’s a good blog about it by Adam Maxwell. It’s a unique identifier for a web resource. e.g. a page or an image on a page. So if you look at the HTTP response headers when you go to a website, you should see unique ETags for every resource returned for that page. They are used for optimizing performance by caching.
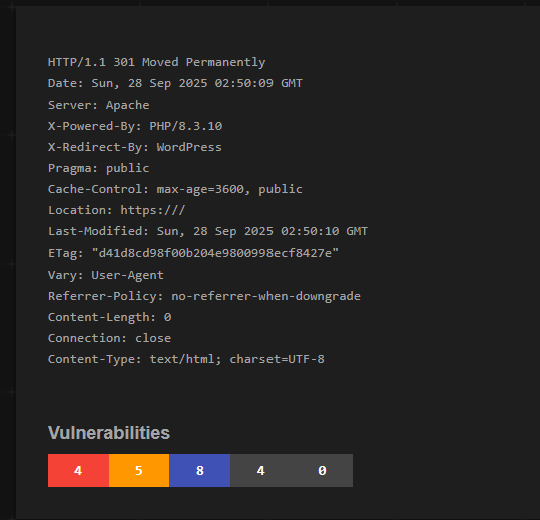
I had a dig around the alert and all the meta data within it. I found we have a detection in one of our internet monitoring tools looking for a file hash in the wild. How effective that is or what value that provides is debatable. I searched the hash on Shodan and got nearly 4,000 hits. Filtering the results by the product flagged in the alert narrowed it down to nearly 2,000 hits. Not that useful.
So, the detection is looking for a file hash on the web/dark web and Shodan lists that same string as an ETag in a HTTP response header from the IP address in the alert.
Without any respectable data analysis, I can see in Shodan that all the HTTP Response headers with the same ETag have the same product and response message, "HTTP/1.1 301 Moved Permanently”. Perhaps this is all related and I am actually onto something? No. Turns out this is the MD5 hash of an empty string.....



